Establishing a Secure Lab Environment
Today's computer labs are subject to various kinds of malicious activities ranging from cyber criminals launching denial of service attacks on major commercial websites to users damaging the equipment. Every year these activities cost academic institutions and the general public millions of dollars. To get the situation under control and protect themselves against accusations of negligence, lab managers need to establish a secure lab environment. Lab Management Systems is a major component of the secure lab environment.
Here we will explain how to use VeraLab to make your computer lab secure
-
Security Threats
A computer lab can become a target as well as an instrument of unwanted activity. The following paragraphs identify the major threats.
Threat 1. Computer Crime
A poorly supervised computer lab is similar to a loaded gun left on a street. A wide range of dangerous activities can be performed from a workstation connected to the Internet. Denial of service attacks, virus distribution, data tampering in corporate information systems, unauthorized access to bank accounts, identity theft, and unsolicited commercial email are just a few of them. With the large number of users coming to the lab, it is a certainty that at some point, a person with malicious intent will attempt to use the lab?s equipment to perform their deeds. With no user tracking system in place, cyber crimes can be performed anonymously.
As a result of attacks on the largest web retailers, cyber crime cost businesses tens of millions of dollars in lost revenue due to site downtime and consumer confidence issues. Consumers are less likely to provide credit card numbers and other personal information if they believe the site is non-secure. Reported losses from cyber crime totaled $455.8 million in 2002. The actual amount is likely much higher.
In comparison, the owner of the gun is responsible for providing safe storage; otherwise this is a negligent conduct (Long v. Turk, 962 P.2d 1093, Kansas Supreme Court 1998; Estate of Heck v. Stoffer, No. 02A03-0007-CV-267, Supreme Court of Indiana). With large amounts of money at stake, lab administrators must protect themselves from charges of negligent conduct in case an attack is launched from their facility.
There is also a chance that the organization owning the computer lab will itself fall victim to a hacker attack. An average academic institution runs Accounting, Human Resource, Learning Management and other information systems. It is even easier to attack a local information system since computer labs are located within the security perimeter.
Lab managers need to ensure that equipment in the lab cannot be used for criminal activity. Although no solution can give a total guarantee, managers do have the capability to minimize the likelihood of disaster, protect themselves against accusations of negligent conduct, and provide efficient means of investigation for lab personnel and law enforcement.
Corporate IT departments are already armed with an impressive variety of security tools such as firewalls, vulnerability assessment applications, intrusion detection software, etc. These tools help protect computers against hacker attacks and identify computers from which the attacks have been launched. The remaining problem to be solved is how to further identify a user in a multi-user environment, prevent him/her from accessing workstations in the future, and establish usage policies that discourage users from performing unwanted activities.
This is where Lab Management Systems, with their ability to manage access to computer resources, collect usage history, identify abusers, maintain alert lists, and remotely supervise user activities come into play.
Threat 2. Unwanted user activity
The following activities fall under this category:
- Illegal activities such as terrorism-related data exchange and content publication, illegal file sharing, and exchange of child pornography.
- Lawful activities offending other users or resulting in waste of computer resources such as browsing porn sites, using instant messengers, playing computer games, and running non-business-related applications.
To counter these activities, lab employees must be able to prevent launching certain software applications, maintain the list of known violators, and maintain and query user access logs. In exceptional cases, administrators should be able to view remotely a report displaying the software launched by the user, take a snapshot of the user's screen, and remotely shut down applications on user machines when necessary. Lab Management Systems, with software metering, surveillance, and user tracking capabilities will address these needs.
Threat 3. Damage and theft of assets
An inherent challenge in owning and running a multi-user environment is the high degree of negligence among users, due to perceived lack of ownership and responsibility. Irresponsible or disgruntled users often, willfully or not, damage workstations and other equipment in the lab.
A poorly supervised computer lab also provides a wealth of opportunity for theft. Without proper supervision, a user can easily remove and steal computer parts, which can then be sold through online auctions and message boards.
To be proactive, computer labs need to establish policies discouraging users from negligent/aggressive behavior and theft by providing better access control to the lab, tracking users' presence in the lab, and controlling users' access to computer resources. This is where a Lab Management System becomes invaluable.
-
Secure Lab Environment
To successfully counter these threats, a computer lab needs to implement a set of measures aimed to achieve a secure lab environment. The measures include: Controlled access to computer rooms and workstations. Only registered users should be allowed in the room. To identify a user, some form of ID needs to be presented. When users bring guests, their presence should be recorded. Unattended workstations should be locked. Lab assistants should be able to force a user out of the workstation by locking the workstation from the control center.
User registrations logs. All user registrations should be logged. Lab employees should be able to identify who used a workstation at any given time and what other workstations were used by the same person.
Alerts when known violators try to access workstations. After violators are identified, lab employees should be able to add them to an Alert List so that the next time a violator attempts to sign in, lab employees will be alerted. Surveillance. In critical cases, lab employees should be able to query the list of applications currently open on a user machine and take a snapshot of a user's display.
Ability to prevent launching certain applications. Users should not be able to launch most popular 'junkware' such as games, chat clients, file sharing clients, etc. Once such an application is launched, it should be automatically shut down by the system. Lab employees should be able to manually shut down applications on user machines from the control center.
-
VERALAB - A Secure Lab Environment Solution
VeraLab Lab Management System is designed as a security-centric application. A computer facility equipped with VeraLab will satisfy all the criteria of a secure lab environment.
Access Control
The lab assistant controls access to workstations by signing-in a user to a workstation from a Lab Assistant Dashboard. The Dashboard may be integrated with a card reader to read data from student ID cards. If the client needs a higher level of authentication, VeraLab Inc. will help develop an ID validation plugin module to verify student IDs against a student database of the client's choice.
Figure 1. Lab Assistant Dashboard.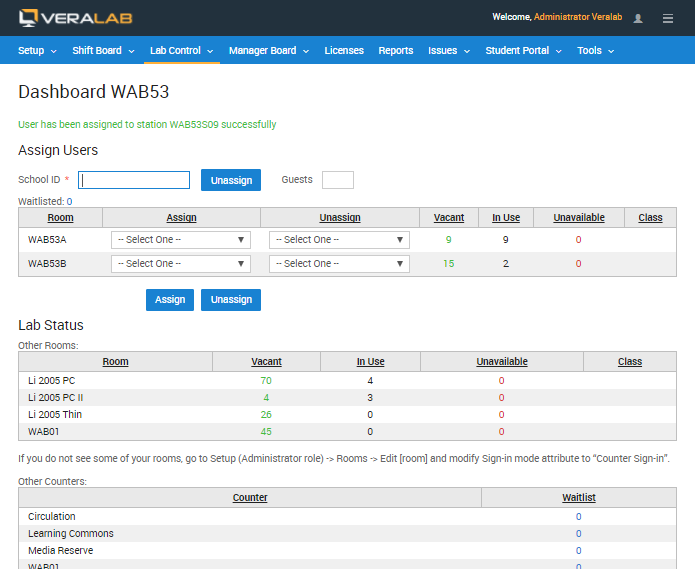
All the information about user sign-in and sign-out is stored in the access log in the database. The lab assistant can record the number of guests accompanying a user.
Locking
Workstations can be locked and unlocked from the Lab Assistant Dashboard. When a workstation is locked, VeraLab Guard, a security component installed on a user's machine, turns off the mouse and keyboard. VeraLab provides three locking modes allowing lab managers to choose the appropriate security policy:
Figure 2. A workstation locked by VeraLab Guard.
'Strict' mode: A workstation is kept locked until the lab assistant signs-in a user. Once the user is signed in, the workstation is automatically unlocked. When the user is signed out, the workstation is automatically locked again. Lab assistants can always lock and unlock the workstation on-demand.
'Liberal' mode: An unattended workstation is kept unlocked. Lab assistants can always lock and unlock the workstation on demand. If the workstation has been locked, it is automatically unlocked once the user is signed in.
'No locking' mode: Lab assistants cannot lock the workstation.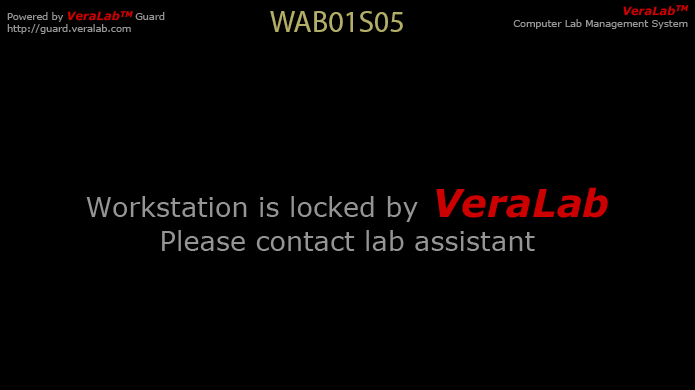
Locking modes are applied on a lab level and can be overridden on a room or workstation level.
Access Log Analysis
Lab employees can search student registrations using various search criteria when it is necessary to identify which user occupied a particular workstation or which workstations have been occupied by a particular user.
Figure 3. User registration search screen.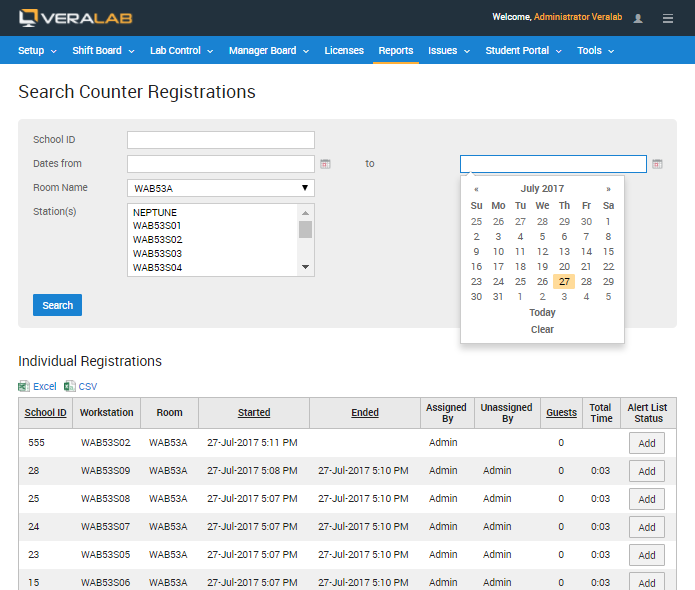
Alert List
VeraLab maintains 'Alert List', allowing lab employees to keep track of known violators. Once a violator is identified, she/he can be added to the 'Alert List'. The system will alert the lab assistant when she/he tries to sign in a user from the Alert List to a workstation. Several alert levels can be associated with the Alert List entry to allow establishment of a clear policy on handling various kinds of violations.
Figure 4. Alert list management console.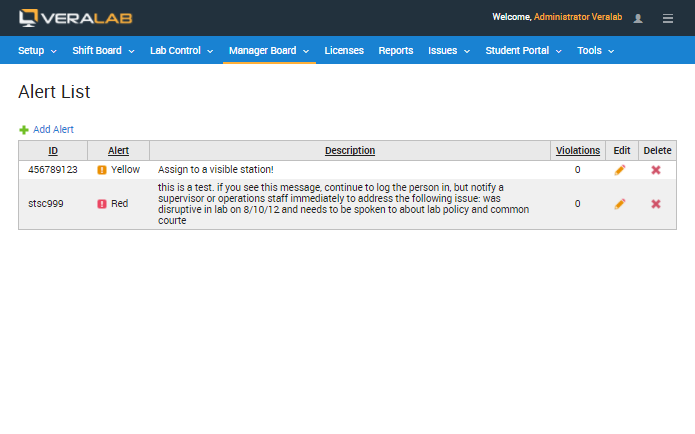
Surveilance
In case of suspicious activity, a trusted VeraLab administrator can remotely download the list of applications currently run by a user or even take a snapshot of a user's screen. This can be used later as evidence.
Figure 5. Screenshot from a user workstation taken remotely.Figure 6. List of the applications running on a user's machine.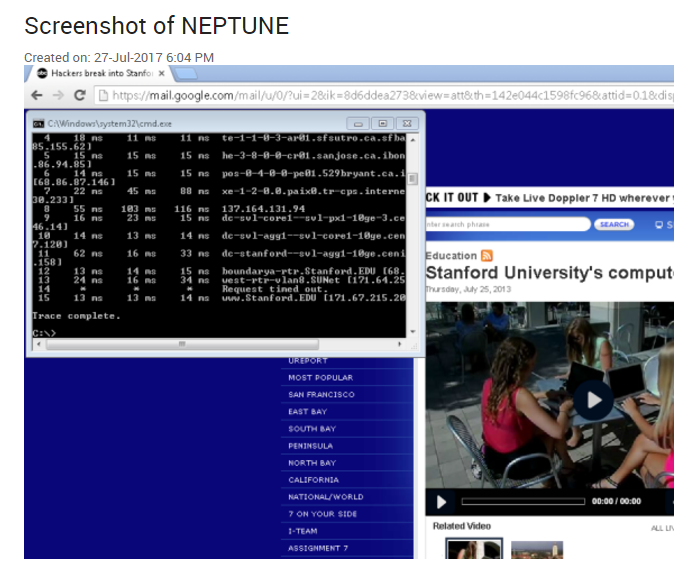
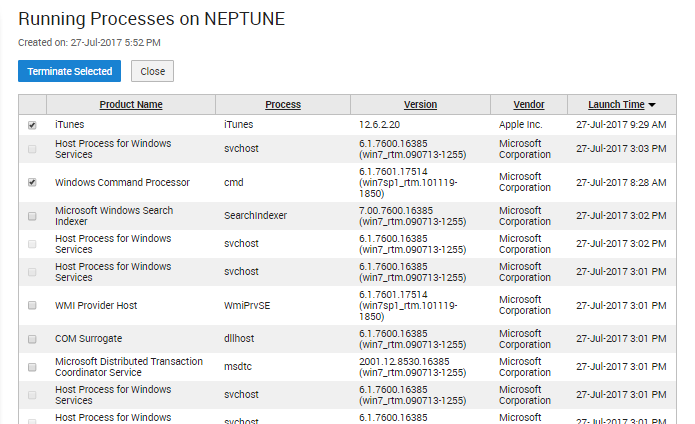
If a user runs an unauthorized application, lab assistants can shut the application down remotely from the Lab Assistant Dashboard.
Software Metering
VeraLab can prevent users from launching unwanted software. A relatively small number of commonly used chat clients, file sharing applications, and games cause a major waste of computer time. Such applications can be added to the 'Restricted Applications List', and in a few seconds after they are launched, VeraLab Guard will automatically shut them down.
Figure 7. VeraLab Guard closing a restricted application.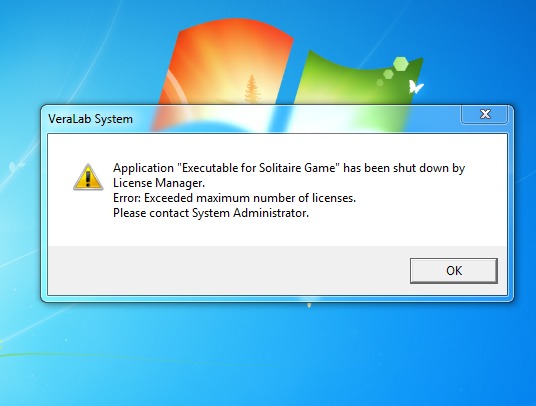
VeraLab Inc. is an innovative software company located in Silicon Valley, CA. Our core business is Computer Lab Management Systems. Our flagship product is VeraLab, a comprehensive lab management suite targeted for academic institutions and corporate training centers. To find out more about VeraLab, please visit VeraLab Home Page.




